实战构建一个满足苹果要求的HTTPS后台服务
1.HTTPS基本概述
为什么需要使用HTTPS, 因为HTTP不安全
1.传输数据被中间人盗用, 信息泄露
2.数据内容劫持, 篡改
2.HTTPS配置语法
Syntax: ssl on | off;
Default: ssl off;
Context: http, server
Syntax: ssl_certificate file;
Default: —
Context: http, server
Syntax: ssl_certificate_key file;
Default: —
Context: http, server3.HTTPS配置场景
配置苹果要求的证书
1.服务器所有连接使用TLS1.2以上版本(openssl 1.0.2)
2.HTTPS证书必须使用SHA256以上哈希算法签名
3.HTTPS证书必须使用RSA 2048位或ECC256位以上公钥算法
4.使用前向加密技术
秘钥生成操作步骤
1.生成key密钥
2.生成证书签名请求文件(csr文件)
3.生成证书签名文件(CA文件)
1.检查当前环境
//openssl必须是1.0.2
[root@Nginx ~]# openssl version
OpenSSL 1.0.2k-fips 26 Jan 2017
//nginx必须有ssl模块
[root@Nginx ~]# nginx -V
--with-http_ssl_module
[root@Nginx ~]# mkdir /etc/nginx/ssl_key -p
[root@Nginx ~]# cd /etc/nginx/ssl_key2.创建私钥
[root@Nginx ssh_key]# openssl genrsa -idea -out server.key 2048
Generating RSA private key, 2048 bit long modulus
.....+++
//记住配置密码, 我这里是1234
Enter pass phrase for server.key:
Verifying - Enter pass phrase for server.key:3.生成使用签名请求证书和私钥生成自签证书
[root@Nginx ssl_key]# openssl req -days 36500 -x509 \
-sha256 -nodes -newkey rsa:2048 -keyout server.key -out server.crt
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:WH
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:edu
Organizational Unit Name (eg, section) []:SA
Common Name (eg, your name or your server's hostname) []:bgx
Email Address []:bgx@foxmail.com4.配置Nginx
[root@Nginx ~]# cat /etc/nginx/conf.d/ssl.conf
server {
listen 443;
server_name localhost;
ssl on;
index index.html index.htm;
#ssl_session_cache share:SSL:10m;
ssl_session_timeout 10m;
ssl_certificate ssl_key/server.crt;
ssl_certificate_key ssl_key/server.key;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
location / {
root /soft/code;
access_log /logs/ssl.log main;
}
}5.测试访问, 由于该证书非第三方权威机构颁发,而是我们自己签发的,所以浏览器会警告
6.以上配置如果用户忘记在浏览器地址栏输入https://那么将不会跳转至https, 需要将访问http强制跳转https
[root@Nginx ~]# cat /etc/nginx/conf.d/ssl.conf
server {
listen 443;
server_name localhost;
ssl on;
index index.html index.htm;
#ssl_session_cache share:SSL:10m;
ssl_session_timeout 10m;
ssl_certificate ssl_key/server.crt;
ssl_certificate_key ssl_key/server.key;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
location / {
root /soft/code;
}
}
server {
listen 80;
server_name localhost;
rewrite ^(.*) https://$server_name$1 redirect;
}7.检查是否支持苹果要求ATS协议
//仅能在苹果终端上使用
$ nscurl --ats-diagnostics --verbose https://192.168.69.1134.Https公有云实践
在云上签发各品牌数字证书,实现网站HTTPS化,使网站可信,防劫持、防篡改、防监听。并进行统一生命周期管理,简化证书部署,一键分发到云上产品。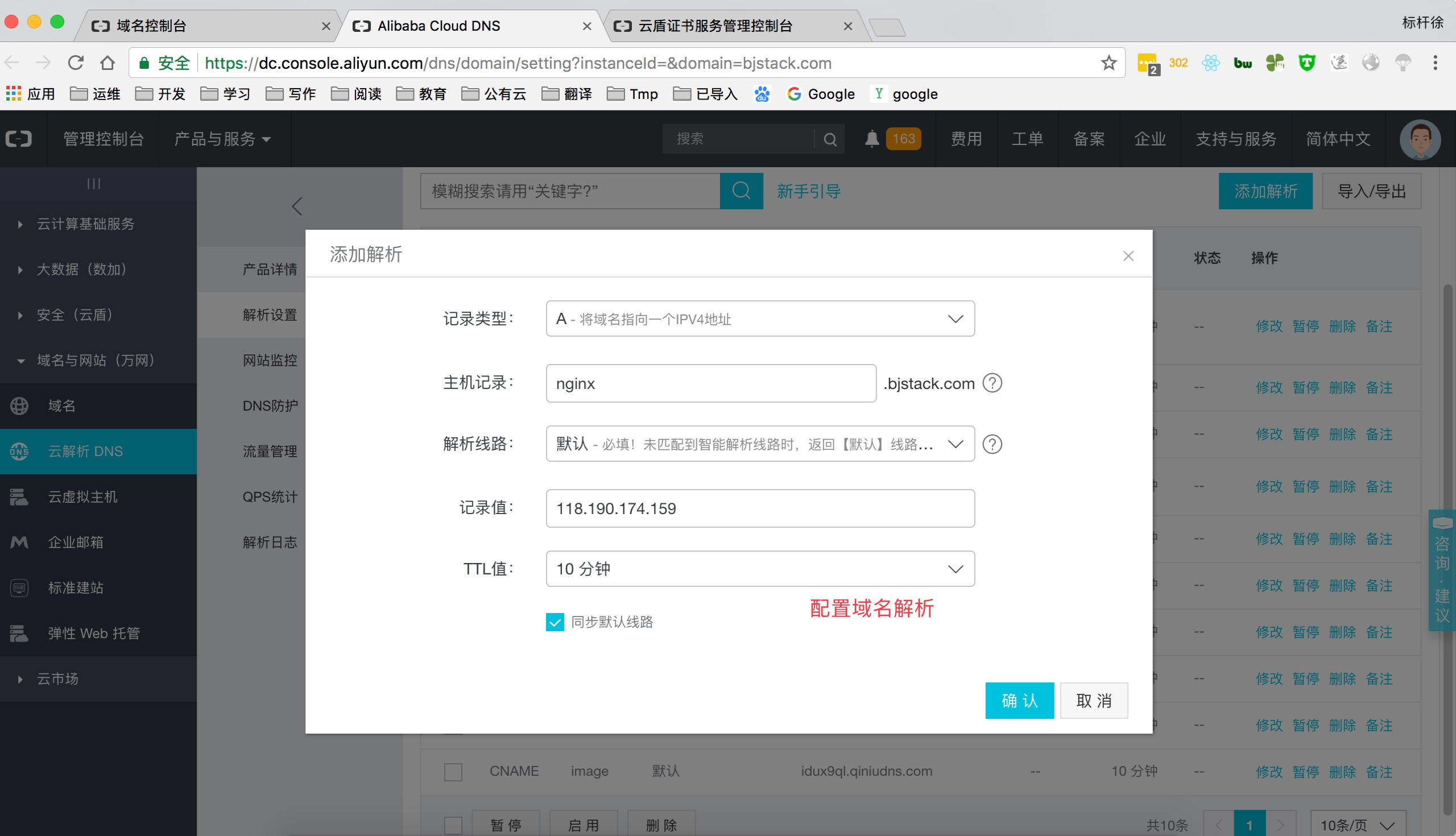
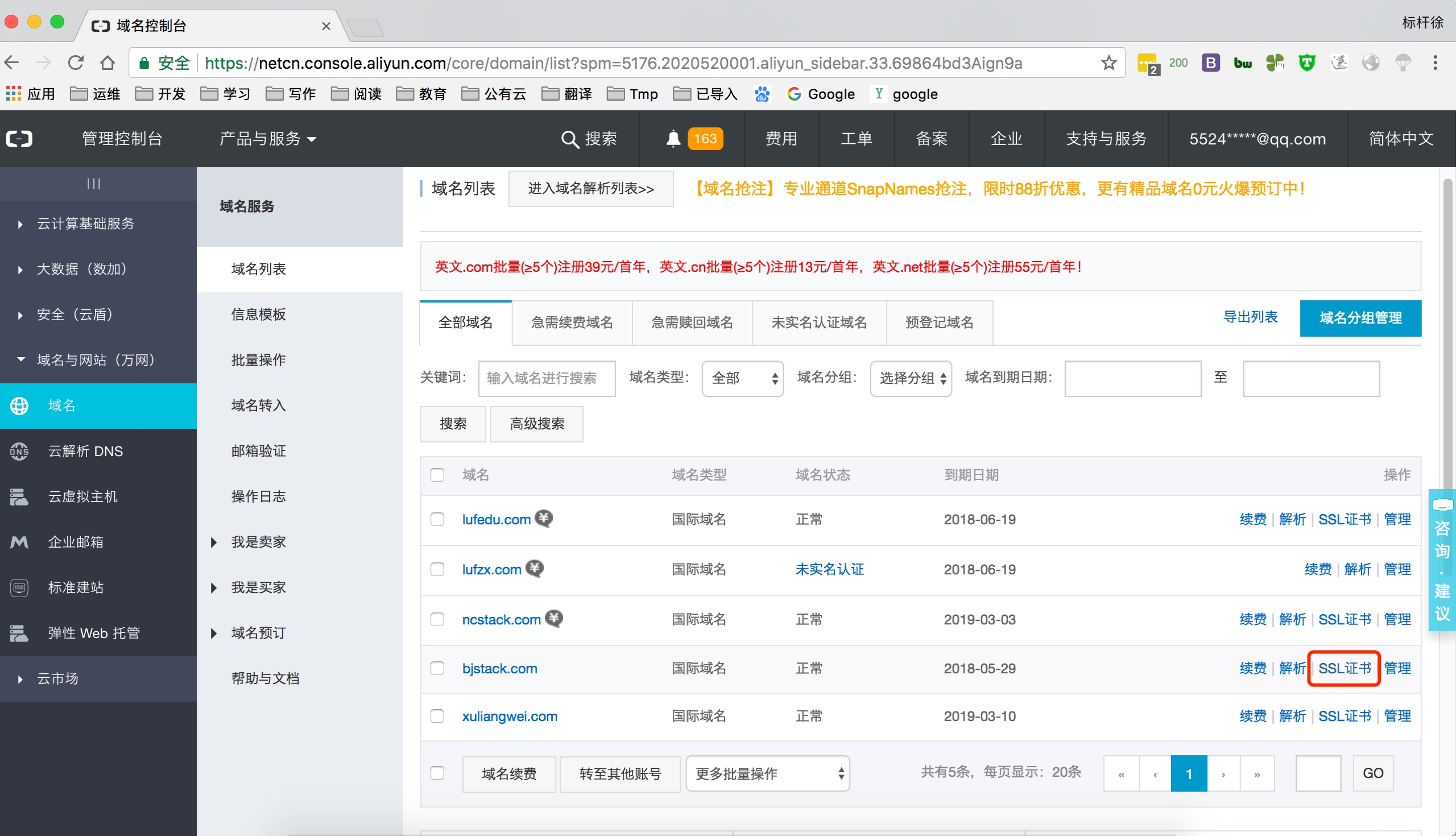
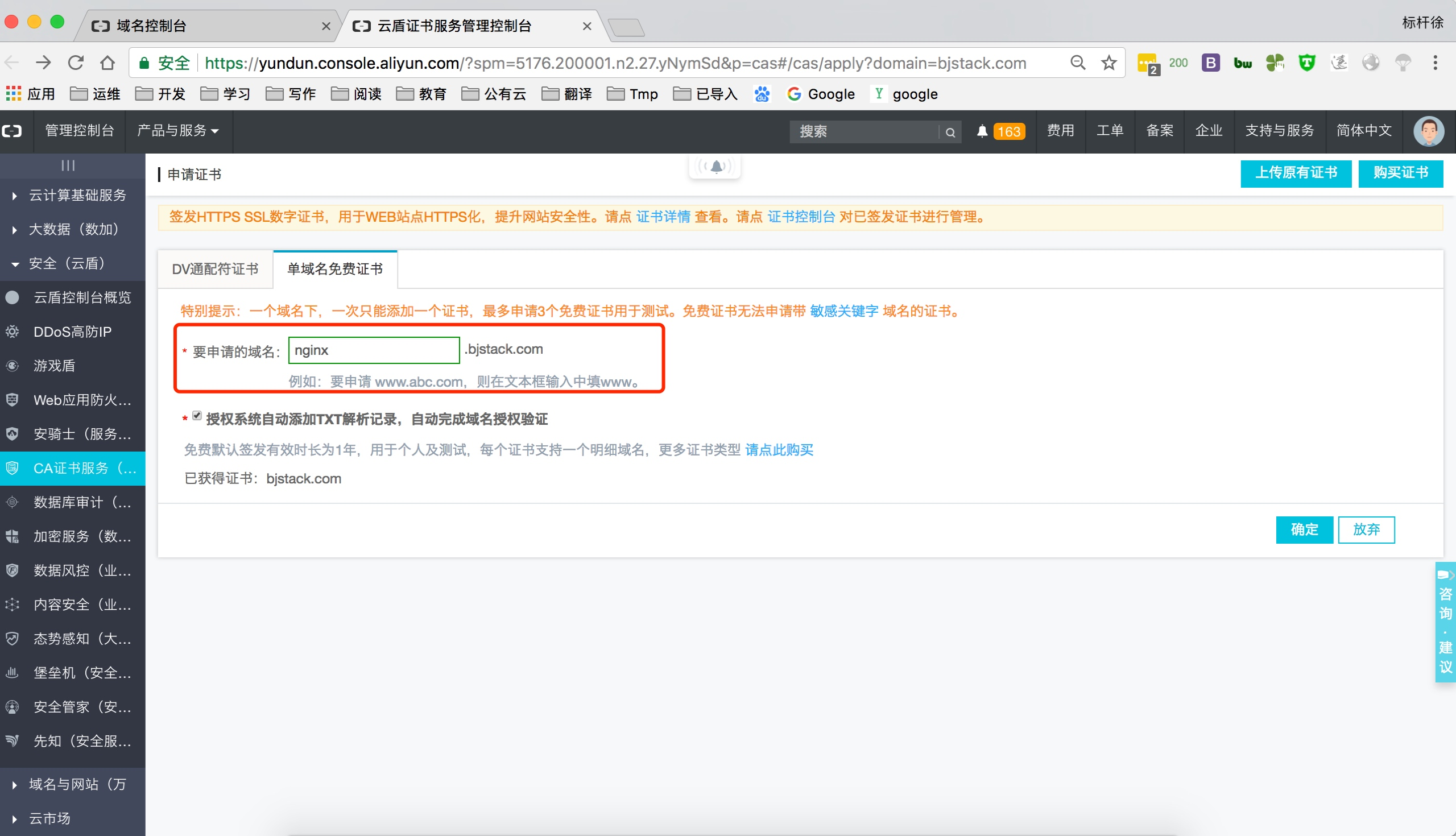
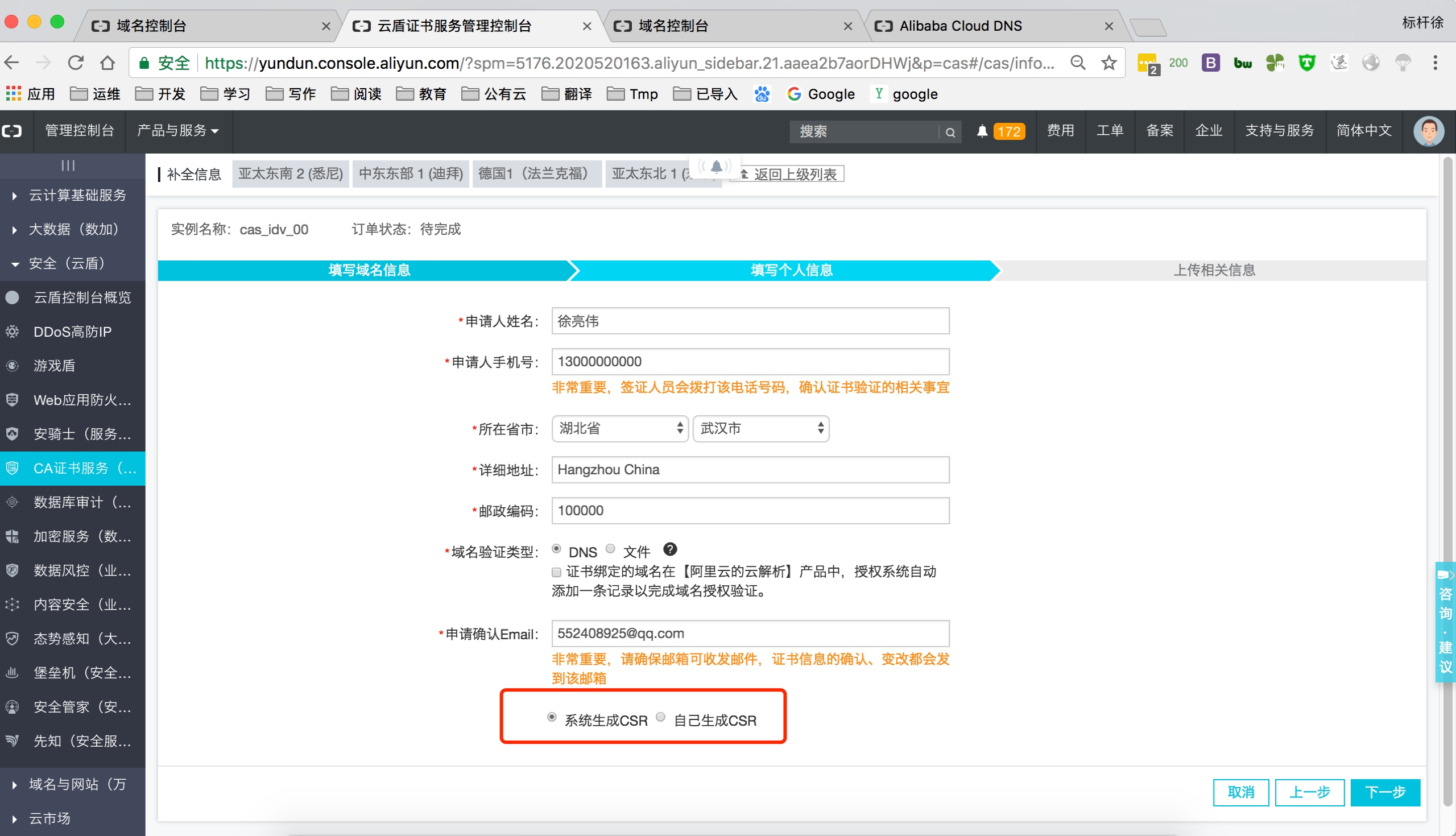
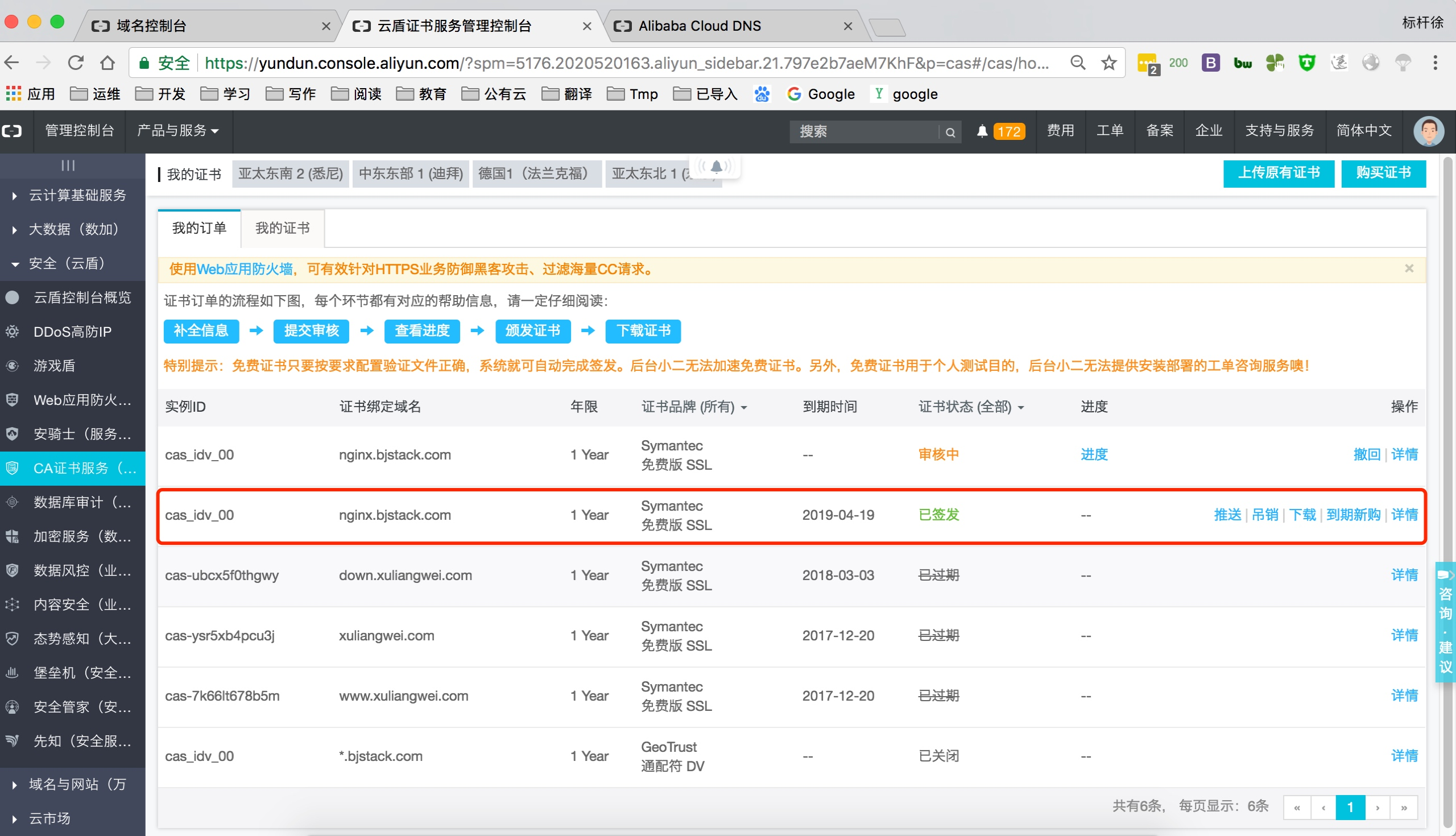
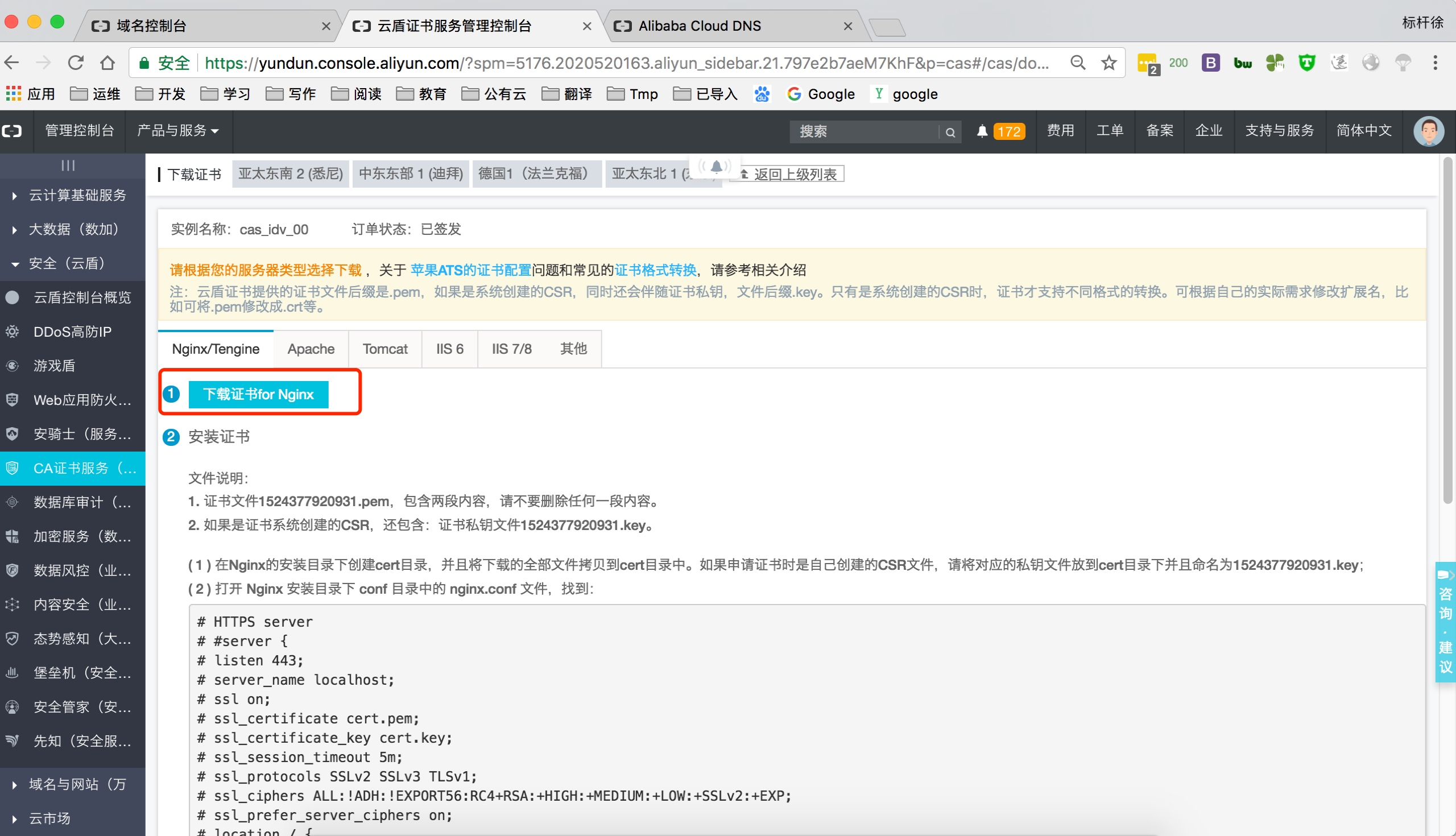
上传阿里云证书, 并解压
[root@Nginx ssl_key]# rz
rz waiting to receive.
Starting zmodem transfer. Press Ctrl+C to cancel.
Transferring 1524377920931.zip...
100% 3 KB 3 KB/sec 00:00:01 0 Errors
//解压
[root@Nginx ssl_key]# unzip 1524377920931.zip
配置nginx https
[root@Nginx conf.d]# cat ssl.nginx.bjstack.com.conf
server {
listen 443;
server_name nginx.bjstack.com;
index index.html index.htm;
ssl on;
ssl_session_timeout 10m;
ssl_certificate ssl_key/1524377920931.pem;
ssl_certificate_key ssl_key/1524377920931.key;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
location / {
root /soft/code;
}
}
server {
listen 80;
server_name nginx.bjstack.com;
rewrite ^(.*) https://$server_name$1 redirect;
}测试访问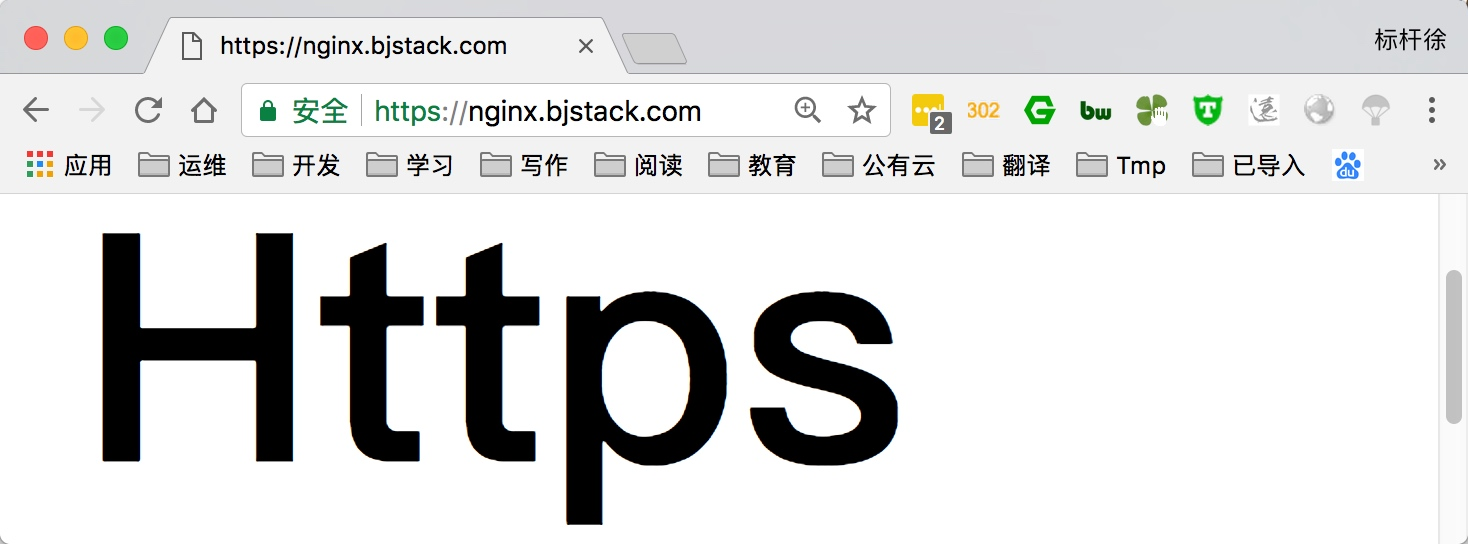
使用腾讯云ATS检测工具检查是否满足苹果IOS要求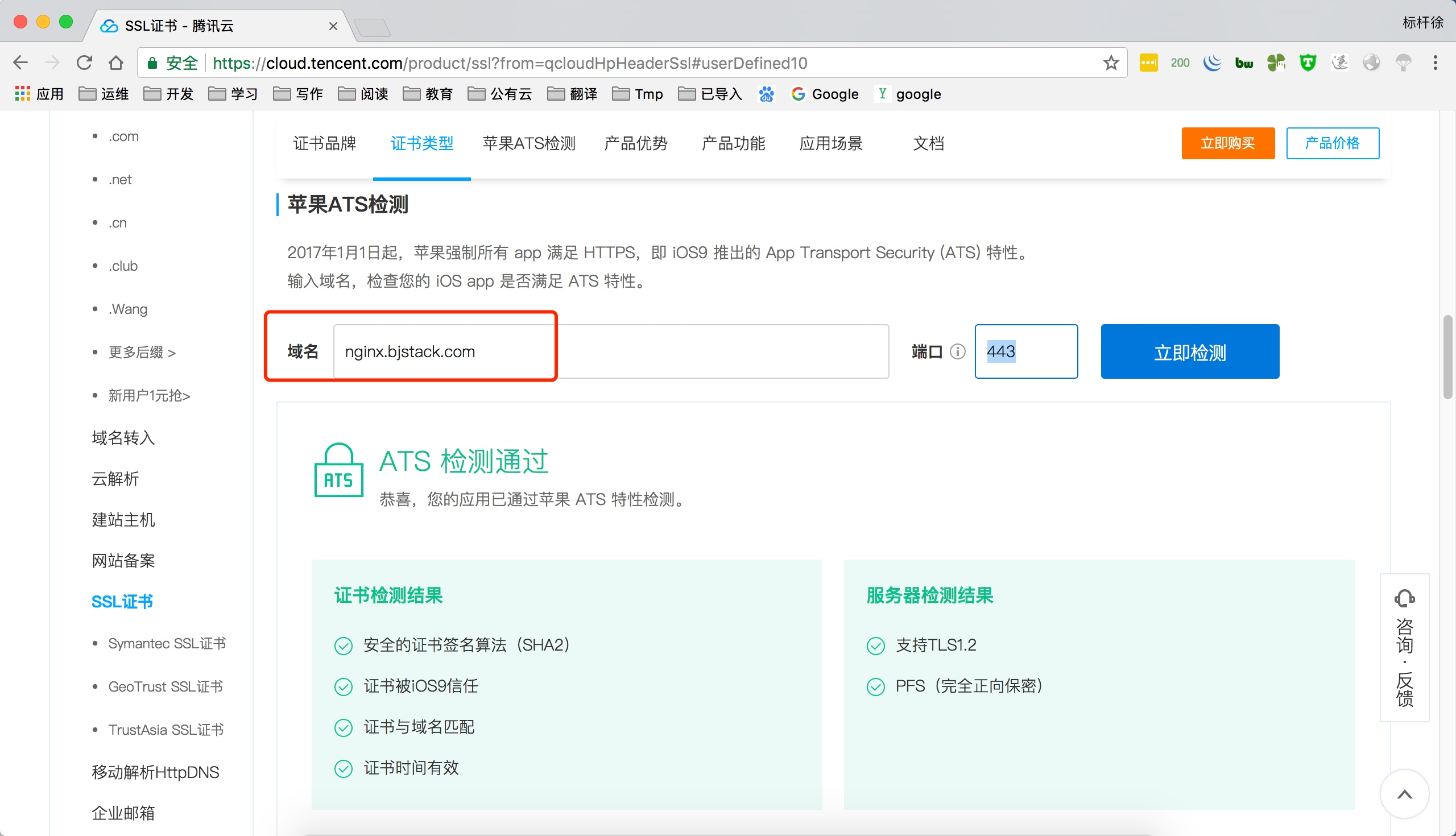
文档更新时间: 2019-07-09 12:52 作者:李延召
